RemoteIoT SSH AWS Example: A Comprehensive Guide To Secure Access
Ever wondered how to secure your IoT devices using SSH on AWS? You’re not alone. RemoteIoT SSH AWS example is a topic that’s been buzzing around tech circles lately. As more businesses and individuals rely on cloud-based solutions, ensuring secure access has become a top priority. In this guide, we’ll break down everything you need to know about setting up secure SSH connections for your IoT devices on AWS.
Think of it this way: your IoT devices are like your digital pets, and SSH is their leash. Without proper control, these devices could run wild, exposing sensitive data. But don’t worry, we’ve got you covered. This guide will walk you through the process step by step, making sure your IoT setup is as secure as Fort Knox.
By the end of this article, you’ll have a solid understanding of how RemoteIoT SSH AWS works, the best practices to follow, and the tools you’ll need to implement it. So buckle up, because we’re about to dive deep into the world of secure IoT access!
Read also:Unveiling The Potential Of Sotwe Turk Ifsa
Before we jump into the nitty-gritty, let’s take a look at what we’ll cover in this guide. Here’s a quick rundown of the topics:
- What is RemoteIoT SSH AWS?
- The Setup Process
- Security Tips for RemoteIoT SSH
- Tools You’ll Need
- Troubleshooting Common Issues
- Best Practices for Secure Access
- Scalability Considerations
- Cost Analysis
- Real-World Examples
- Conclusion
What is RemoteIoT SSH AWS?
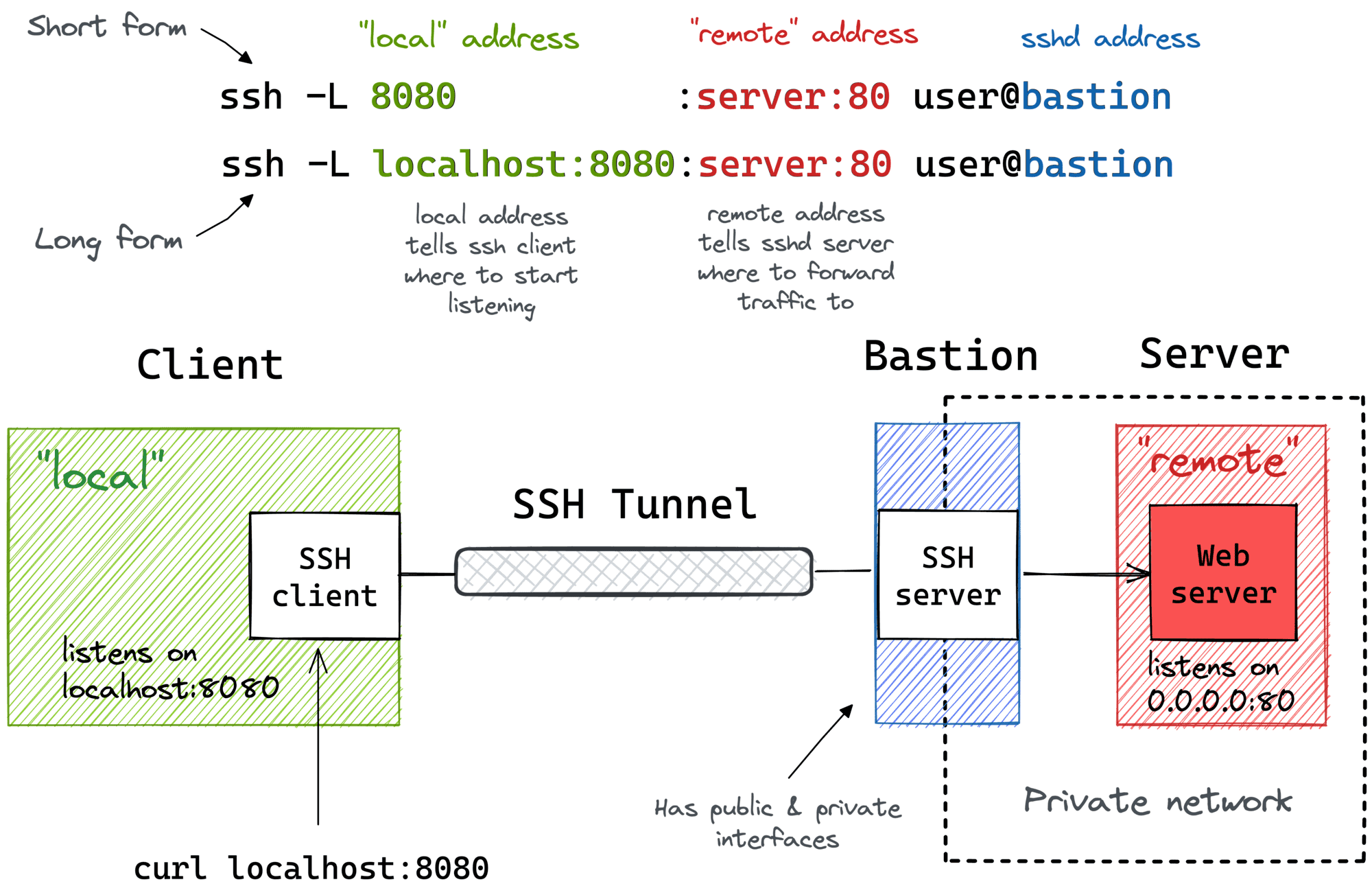
Let’s start with the basics. RemoteIoT SSH AWS refers to the process of securely accessing IoT devices through SSH (Secure Shell) protocols, hosted on Amazon Web Services (AWS). It’s like giving your devices a VIP pass to communicate with your cloud infrastructure without any snooping eyes.
How Does It Work?
SSH creates an encrypted tunnel between your IoT device and the AWS server. This tunnel ensures that all data transmitted is safe from prying eyes. AWS, being one of the most reliable cloud platforms, provides the infrastructure needed to manage and secure these connections.
Here’s a quick breakdown of the process:
- Generate SSH keys on your local machine.
- Upload the public key to your AWS instance.
- Connect to your IoT device via SSH using the private key.
It’s like setting up a secret handshake between your device and AWS. Cool, right?
The Setup Process
Now that you know what RemoteIoT SSH AWS is, let’s talk about how to set it up. The process might seem a bit overwhelming at first, but trust me, it’s easier than you think.
Read also:Discover Chris Brown Net Worth Age And Personal Life 2023
Step 1: Create an AWS Account
If you don’t already have an AWS account, head over to the AWS website and sign up. It’s free to start, and you’ll only pay for what you use. Once you’re all set up, create an EC2 instance. Think of it as your digital workspace where all the magic happens.
Step 2: Generate SSH Keys
SSH keys are like your digital ID cards. To generate them, use a tool like PuTTYgen (for Windows) or ssh-keygen (for Linux/Mac). Save both the private and public keys in a secure location. The public key will be uploaded to AWS, while the private key stays on your local machine.
Step 3: Configure Security Groups
Security groups act as firewalls for your EC2 instances. Make sure to allow SSH traffic (port 22) in your security group settings. This step ensures that only authorized devices can connect to your instance.
Step 4: Connect via SSH
With everything set up, it’s time to connect. Open your terminal (or PuTTY for Windows) and use the following command:
ssh -i /path/to/your/private/key.pem ec2-user@your-ec2-public-ip
Replace the placeholders with your actual key path and EC2 instance IP. And just like that, you’re in!
Security Tips for RemoteIoT SSH
Now that you know how to set up SSH on AWS, let’s talk about securing it. Security is crucial when dealing with IoT devices, as they often handle sensitive data.
1. Use Strong Passwords
Even though SSH keys provide an extra layer of security, it’s always a good idea to use strong passwords. Avoid using common phrases or easily guessable words.
2. Disable Root Login
Root login allows full administrative access, which can be risky if compromised. Disable it and create a separate user with limited privileges.
3. Update Regularly
Keep your software and firmware up to date. Updates often include security patches that protect against the latest threats.
4. Monitor Logs
Regularly check your server logs for any suspicious activity. Tools like AWS CloudTrail can help you keep track of all API activity.
Tools You’ll Need
Having the right tools makes all the difference. Here’s a list of essential tools for setting up RemoteIoT SSH on AWS:
- AWS Management Console
- SSH Client (PuTTY, OpenSSH)
- Key Management Software (PuTTYgen, ssh-keygen)
- Monitoring Tools (AWS CloudWatch, CloudTrail)
These tools will streamline your setup process and ensure everything runs smoothly.
Troubleshooting Common Issues
Even with the best preparation, issues can arise. Here are some common problems and how to fix them:
Problem: Connection Refused
This usually happens when the security group settings are incorrect. Double-check that port 22 is open and that your IP address is allowed.
Problem: Permission Denied
This error often occurs when the private key file has incorrect permissions. Make sure the file is only readable by the owner:
chmod 400 /path/to/your/private/key.pem
Problem: Timeout
Timeouts can be caused by network issues or firewall restrictions. Ensure that your local network allows outbound SSH traffic.
Best Practices for Secure Access
Following best practices will help you maintain a secure environment. Here are a few tips:
1. Limit Access
Restrict SSH access to only those who need it. Use IP whitelisting to allow connections from specific addresses.
2. Use Two-Factor Authentication
Add an extra layer of security by enabling two-factor authentication (2FA). AWS provides several options for implementing 2FA.
3. Regular Audits
Perform regular audits of your security settings and user permissions. This ensures that everything is up to date and compliant with security standards.
Scalability Considerations
As your IoT setup grows, scalability becomes a key factor. AWS offers several services to help you scale your infrastructure:
- Auto Scaling: Automatically adjust resources based on demand.
- Elastic Load Balancing: Distribute traffic evenly across multiple instances.
- CloudFormation: Use templates to deploy infrastructure consistently.
These services ensure that your setup can handle increased loads without compromising performance.
Cost Analysis
Cost is always a concern when dealing with cloud services. AWS offers a variety of pricing models to fit different needs:
- On-Demand Instances: Pay for what you use, no upfront costs.
- Reserved Instances: Save money by committing to a specific instance type for a year or more.
- Spot Instances: Bid on unused EC2 instances at a lower price.
Choose the model that best fits your budget and requirements. AWS also provides a cost calculator to help you estimate expenses.
Real-World Examples
Let’s look at some real-world examples of companies using RemoteIoT SSH AWS:
Example 1: Smart Home Solutions
A leading smart home company uses SSH on AWS to securely manage thousands of IoT devices. This setup allows them to monitor and control devices remotely, ensuring customer data remains protected.
Example 2: Industrial IoT
An industrial manufacturer leverages AWS for their IoT infrastructure, using SSH to secure connections between machines and the cloud. This has improved efficiency and reduced downtime.
Conclusion
In conclusion, RemoteIoT SSH AWS is a powerful solution for securing your IoT devices. By following the steps outlined in this guide, you can set up a secure connection that protects your data and ensures smooth operations.
Remember to follow best practices and regularly update your security measures. And don’t forget to monitor your logs for any suspicious activity. If you have any questions or need further clarification, feel free to leave a comment below. Share this guide with your friends and colleagues who might find it useful!
Stay safe out there, and happy coding!